请注意,本文编写于 702 天前,最后修改于 702 天前,其中某些信息可能已经过时。
目录
acme.sh 实现了 acme 协议, 可以从 letsencrypt 生成免费的证书.
主要步骤:
- 安装 acme.sh
- 生成证书
- copy 证书到 nginx/apache 或者其他服务
- 更新证书
- 更新 acme.sh
- 出错怎么办, 如何调试
下面详细介绍.
安装acme.sh
安装很简单, 一个命令:
shellcurl https://get.acme.sh | sh -s email=my@example.com
普通用户和 root 用户都可以安装使用. 安装过程进行了以下几步:
把 acme.sh 安装到你的 home 目录下:
shell~/.acme.sh/
并创建 一个 shell 的 alias, 例如 .bashrc,方便你的使用: alias acme='/root/.acme.sh/acme.sh'
自动为你创建 cronjob, 每天 0:00 点自动检测所有的证书, 如果快过期了, 需要更新, 则会自动更新证书.
生成证书
首先配置域名所属云平台的secretID和Key 以阿里云为例:
1、获取ID/Key
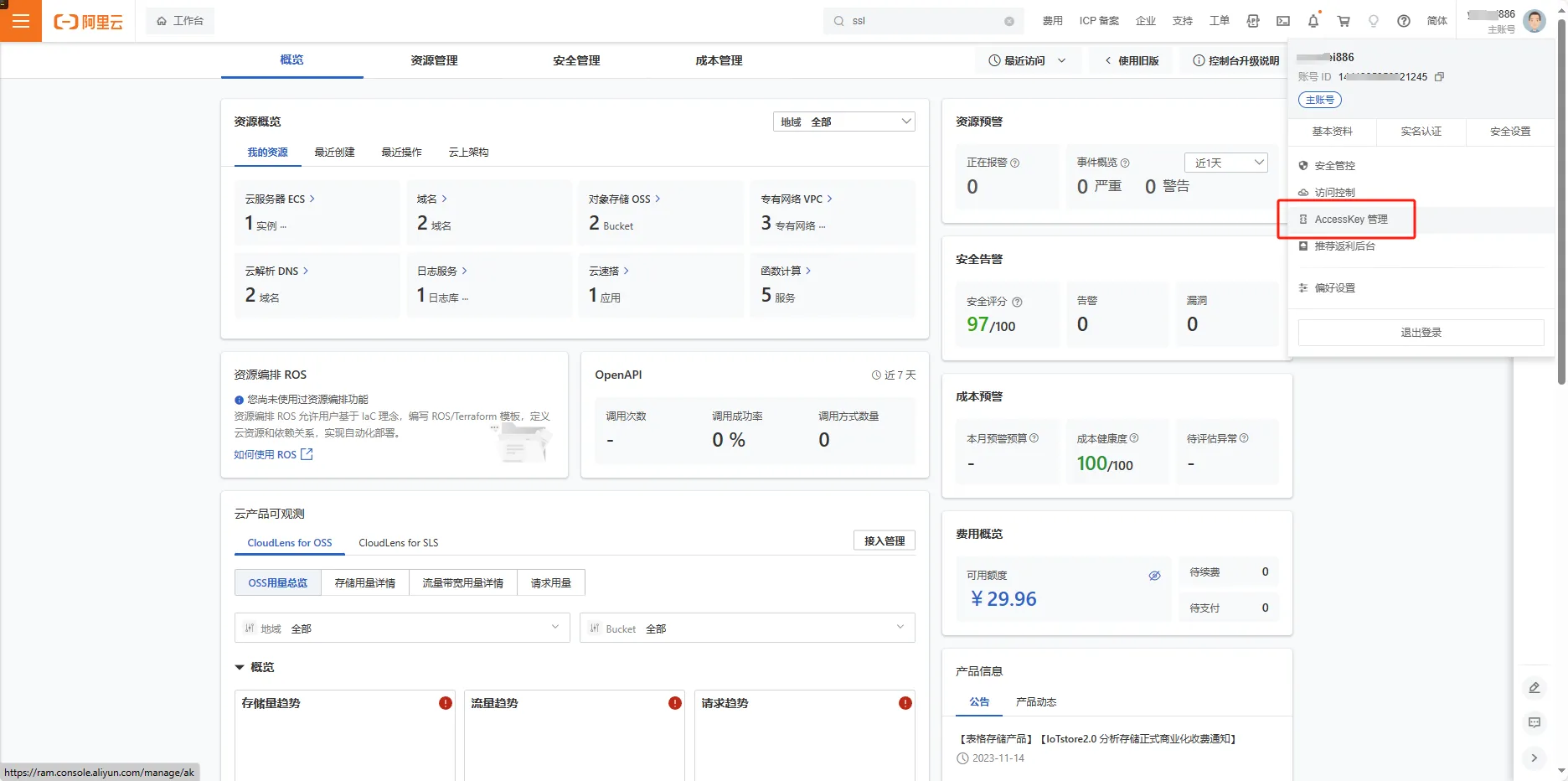
2、生成ID/Key并记录

3、将secretID/Key设置为变量
shellexport DOMAIN="netwebs.top" # 域名 export Ali_Key="123**************7890" # 阿里云RAM用户账户 export Ali_Secret="aBcDEf**********WxYz234" # 阿里云RAM用户密码
4、设置完成后执行命令
shellalias acme='/root/.acme.sh/acme.sh' acme --set-default-ca --server letsencrypt acme --issue -d ${DOMAIN} -d *.${DOMAIN} --dns dns_ali --keylength 2048
5、执行结果如下
shell[Wed Nov 15 11:12:33 CST 2023] Already uptodate! [Wed Nov 15 11:12:33 CST 2023] Upgrade success! [Wed Nov 15 11:12:33 CST 2023] Changed default CA to: https://acme-v02.api.letsencrypt.org/directory [Wed Nov 15 11:12:35 CST 2023] Using CA: https://acme-v02.api.letsencrypt.org/directory [Wed Nov 15 11:12:35 CST 2023] Creating domain key [Wed Nov 15 11:12:35 CST 2023] The domain key is here: /root/.acme.sh/netwebs.top/netwebs.top.key [Wed Nov 15 11:12:35 CST 2023] Multi domain='DNS:netwebs.top,DNS:*.netwebs.top' [Wed Nov 15 11:12:35 CST 2023] Getting domain auth token for each domain [Wed Nov 15 11:12:42 CST 2023] Getting webroot for domain='netwebs.top' [Wed Nov 15 11:12:42 CST 2023] Getting webroot for domain='*.netwebs.top' [Wed Nov 15 11:12:42 CST 2023] Adding txt value: N2X-aJVBfSwx08gyv84heuWkrzpSO3f3eTv7hA-ej4M for domain: _acme-challenge.netwebs.top [Wed Nov 15 11:12:44 CST 2023] The txt record is added: Success. [Wed Nov 15 11:12:44 CST 2023] Adding txt value: vaxfS6xrYITlrpzccuedl7OIDAV5aJeLChdkYas_7JQ for domain: _acme-challenge.netwebs.top [Wed Nov 15 11:12:47 CST 2023] The txt record is added: Success. [Wed Nov 15 11:12:47 CST 2023] Let's check each DNS record now. Sleep 20 seconds first. [Wed Nov 15 11:13:08 CST 2023] You can use '--dnssleep' to disable public dns checks. [Wed Nov 15 11:13:08 CST 2023] See: https://github.com/acmesh-official/acme.sh/wiki/dnscheck [Wed Nov 15 11:13:08 CST 2023] Checking netwebs.top for _acme-challenge.netwebs.top [Wed Nov 15 11:13:08 CST 2023] Please refer to https://curl.haxx.se/libcurl/c/libcurl-errors.html for error code: 35 [Wed Nov 15 11:13:16 CST 2023] Please refer to https://curl.haxx.se/libcurl/c/libcurl-errors.html for error code: 7 [Wed Nov 15 11:13:16 CST 2023] Domain netwebs.top '_acme-challenge.netwebs.top' success. [Wed Nov 15 11:13:16 CST 2023] Checking netwebs.top for _acme-challenge.netwebs.top [Wed Nov 15 11:13:17 CST 2023] Domain netwebs.top '_acme-challenge.netwebs.top' success. [Wed Nov 15 11:13:17 CST 2023] All success, let's return [Wed Nov 15 11:13:17 CST 2023] Verifying: netwebs.top [Wed Nov 15 11:13:18 CST 2023] Pending, The CA is processing your order, please just wait. (1/30) [Wed Nov 15 11:13:24 CST 2023] Success [Wed Nov 15 11:13:24 CST 2023] Verifying: *.netwebs.top [Wed Nov 15 11:13:26 CST 2023] Pending, The CA is processing your order, please just wait. (1/30) [Wed Nov 15 11:13:30 CST 2023] Success [Wed Nov 15 11:13:30 CST 2023] Removing DNS records. [Wed Nov 15 11:13:30 CST 2023] Removing txt: N2X-aJVBfSwx08gyv84heuWkrzpSO3f3eTv7hA-ej4M for domain: _acme-challenge.netwebs.top [Wed Nov 15 11:13:33 CST 2023] Removed: Success [Wed Nov 15 11:13:33 CST 2023] Removing txt: vaxfS6xrYITlrpzccuedl7OIDAV5aJeLChdkYas_7JQ for domain: _acme-challenge.netwebs.top [Wed Nov 15 11:13:36 CST 2023] Removed: Success [Wed Nov 15 11:13:36 CST 2023] Verify finished, start to sign. [Wed Nov 15 11:13:36 CST 2023] Lets finalize the order. [Wed Nov 15 11:13:36 CST 2023] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/1412997226/222282231876' [Wed Nov 15 11:13:38 CST 2023] Downloading cert. [Wed Nov 15 11:13:38 CST 2023] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/0369db5fbdf25a226d544f33d50870f15698' [Wed Nov 15 11:13:39 CST 2023] Cert success. -----BEGIN CERTIFICATE----- MIIE8TCCA9mgAwIBAgISA2nbX73yWiJtVE8z1Qhw8VaYMA0GCSqGSIb3DQEBCwUA MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD EwJSMzAeFw0yMzExMTUwMjEzMzhaFw0yNDAyMTMwMjEzMzdaMBYxFDASBgNVBAMT C25ldHdlYnMudG9wMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvIRu SvlvTkuqkGb7gsAQ0IIj6P5l5CeabReu9pxr/R+W//h0r31pTESI+rRFiSG9588v odEvbl9/Obc******************************************QvR4oEEICfA Qlel50TMhtFYZlosJZnj512ITG6R3WYxHIwAaCV0uxlYEE1IMIsCH7GpuU14FFeu Ju7S7+9Lu2c4SR9n4A3lYeldu/NohHw7ipEl/NE+u+zBSakHUDETIT1O9zsIebHe NOEVG+KyTM7QAY1yIjbSYMcUcMzISrHQ/cylBbiP+bIQ0aPsUa7+V5gA/VvFe7px OtMlEcGBqv6ME0oslwIDAQABo4ICGzCCAhcwDgYDVR0PAQH/BAQDAgWgMB0GA1Ud JQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAMBgNVHRMBAf8EAjAAMB0GA1UdDgQW BBR/Bk2uLfO568Zu6ruz1HsjetLhJjAfBgNVHSMEGDAWgBQULrMXt1hWy65QCUDm H6+dixTCxjBVBggrBgEFBQcBAQRJMEcwIQYIKwYBBQUHMAGGFWh0dHA6Ly9yMy5v LmxlbmNyLm9yZzAiBggrBgEFBQcwAoYWaHR0cDovL3IzLmkubGVuY3Iub3JnLzAl BgNVHREEHjAcgg0qLm5ldHdlYnMudG9wggtuZXR3ZWJzLnRvcDATBgNVHSAEDDAK MAgGBmeBDAECATCCAQMGCisGAQQB1nkCBAIEgfQEgfEA7wB1AEiw42vapkc0D+Vq AvqdMOscUgHLVt0sgdm7v6s52IRzAAABi9D4VzoAAAQDAEYwRAIgZjYfKqC4AxSv 56SEgL5p+6vuboTJdkkiN9MR2Qj8X7MCIGAhNNtNN8VERqssdYjxCDbXo3PLYIri UM06L4ugUSw8AHYAO1N3dT4tuYBOizBbBv5AO2fYT8P0x70ADS1yb+H61BcAAAGL 0PhXNgAABAMARzBFAiAryfwNWJxB05OWn5kF4noQVOXaBeTBzvBRiFZ8BTBixAIh APIgKmVfanIDTHjFeKzOSoJLpnpYFuB2Gssb93Jy6SWlMA0GCSqGSIb3DQEBCwUA A4IBAQCqZF0rpLrAJunKgl5uHuFUXpNRX4YHe1rdyLf/2+J1HEIUyaXpBSIySp4Y Gnd/sjGJGi9a6mhu46jhhwgcCeZY+LIOJqNJnyOVg676syHrMyjEFHi/6MZiPRli 8rODGoe/RsFVIeIE+rlFoJ0IO/+coBX5bLPcZuA2WWdNqvMn3hqXTj/bKDDCVLjS YOTWJdRIfr5QcFGbQIaIBGMNhZ6KZostdSOxHOsXETX+nKiIPGajJqC0O9h/IogP Ck9tDz5SceAbgZollRXlo9/YLUN65PVAH7S+TmKJwq9yRpnY6RTSSu74DJSrfCyp RNH5cJZpX+/nU0YU6ESlwj4L5ICK -----END CERTIFICATE----- [Wed Nov 15 11:13:39 CST 2023] Your cert is in: /root/.acme.sh/netwebs.top/netwebs.top.cer [Wed Nov 15 11:13:39 CST 2023] Your cert key is in: /root/.acme.sh/netwebs.top/netwebs.top.key [Wed Nov 15 11:13:39 CST 2023] The intermediate CA cert is in: /root/.acme.sh/netwebs.top/ca.cer [Wed Nov 15 11:13:39 CST 2023] And the full chain certs is there: /root/.acme.sh/netwebs.top/fullchain.cer
6、证书会被保存在/root/.acme.sh/${DOMAIN}/ 下
其中
fullchain.cer 是证书链
netwebs.top.cer 是${DOMAIN}的域名证书
netwebs.top.key 是${DOMAIN}的域名私钥
ca.cer 是证书颁发机构的CA证书
cer证书更改后缀为.pem即为pem证书
这里生成的key是RSA加密类型的,RSA加密类型适配软件比较多
7、使用
将云平台的域名解析到指定服务器后,就可以使用证书进行https访问了
具体使用方法:https://www.baidu.com/s?wd=nginx%E9%85%8D%E7%BD%AE%E6%B3%9B%E5%9F%9F%E5%90%8D
如果对你有用的话,可以打赏哦
打赏


本文作者:YOUWEI
本文链接:
版权声明:本博客所有文章除特别声明外,均采用 ™ 许可协议。转载请注明出处!
目录